Use case description
A small governmental ISP suspected that confidential information is stolen from its users. The ISP used several commercial security solutions that
found nothing but still, some targeted attacks against the governmental users were performed and succeeded.
Our challange was to mine the network, identify malicious and stealthy attacks and provide defense mechanism to block them.
Our analysis
The network data that we analyzed included Internet browsing activity of the governmental users.
Each day of browsing activity contained 60 millions log records of HTTP (browsing) connections.
Each log was described by hundreds of numeric, nominal and textual parameters. For example, the number of uploaded bytes,
the duration of the HTTP session, the version of the browser of the client, the URL etc,.
We used two of our main technologies for data mining and anomaly detection.
The first method is our Differential Diagnosis technology that is used to analyze the traffic, detect anomalies, characterize them and then use the
characterization to propagate and detect other anomalies. This way we exposed hundreds and even thousands of Trojans in the system.
The following movie presents the Differential Diagnosis in action:
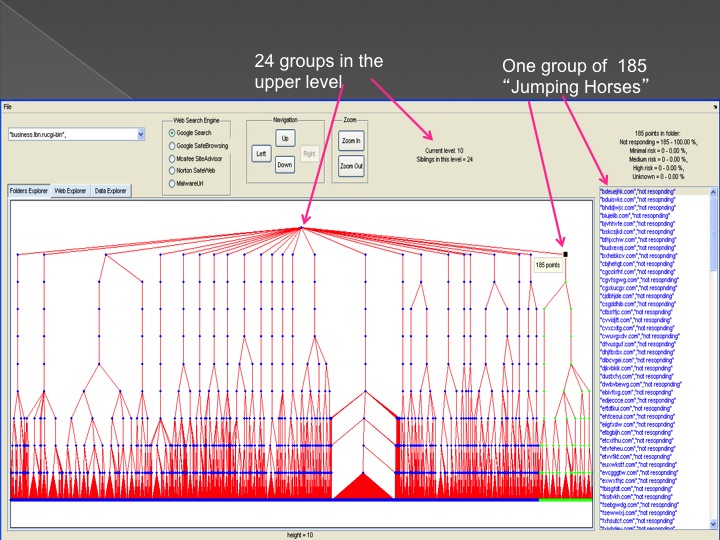
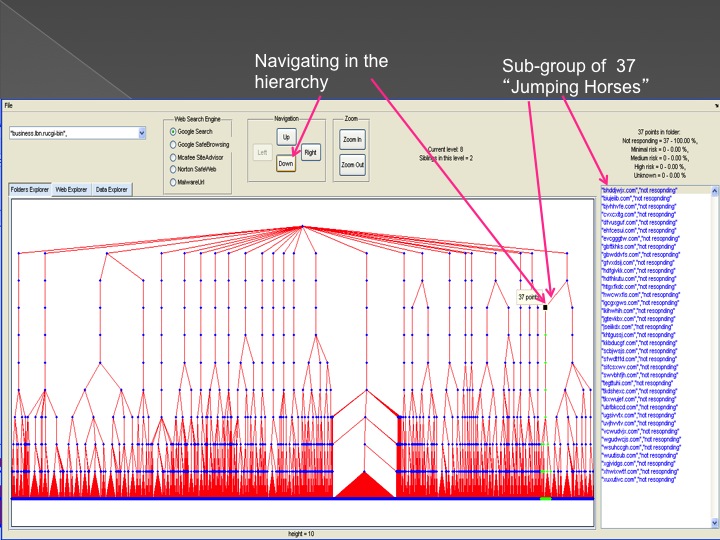
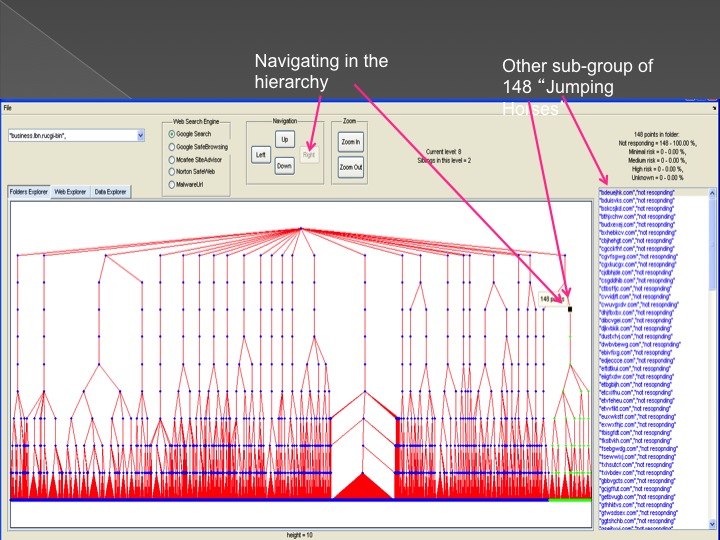
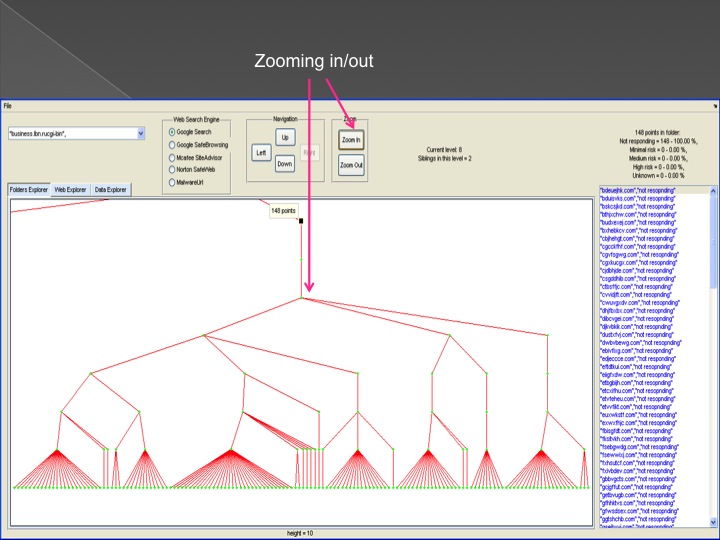
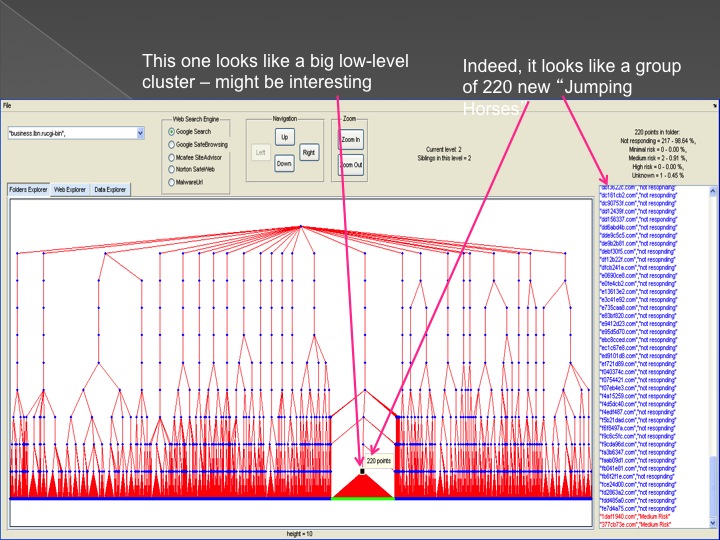
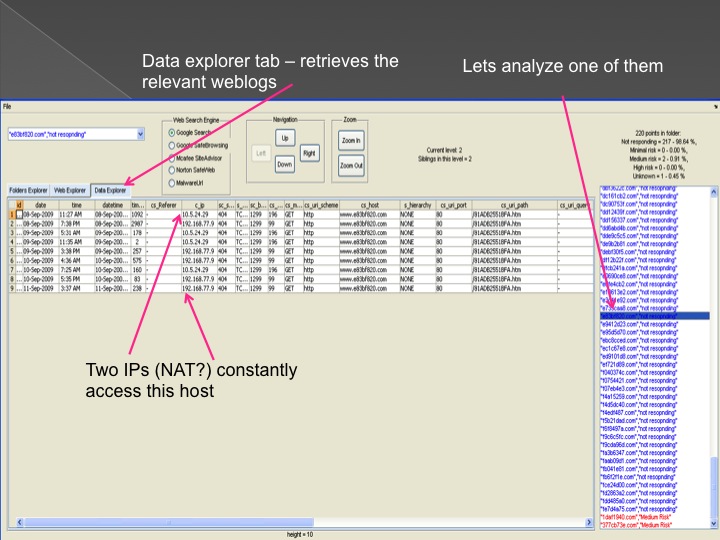
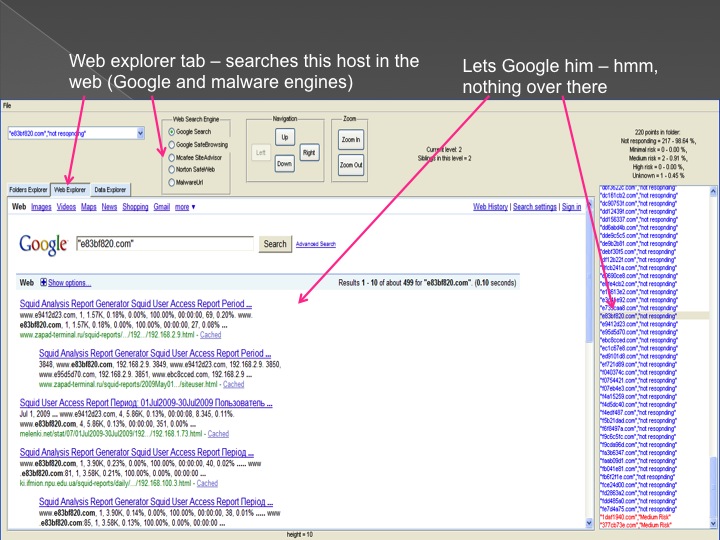
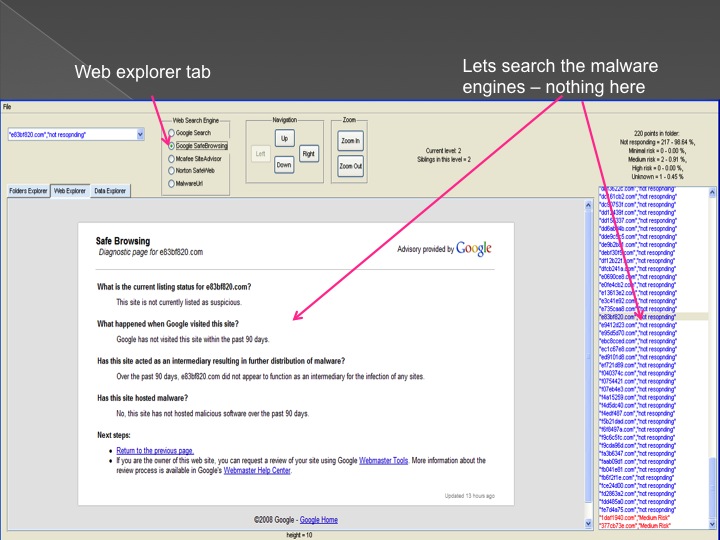
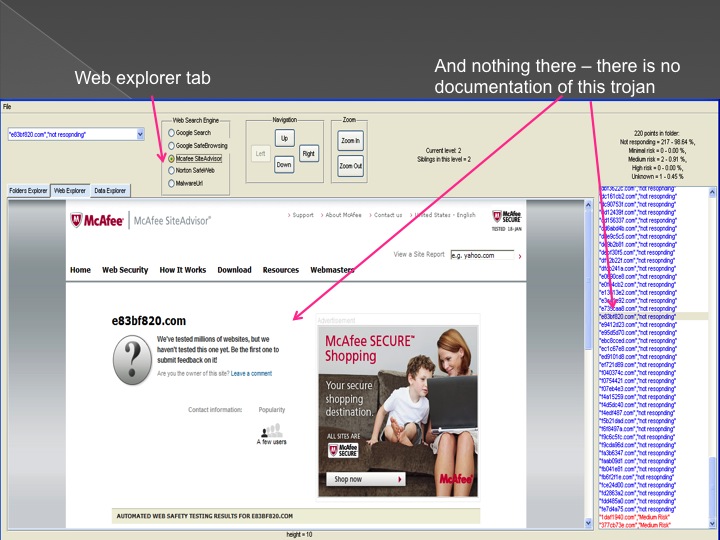
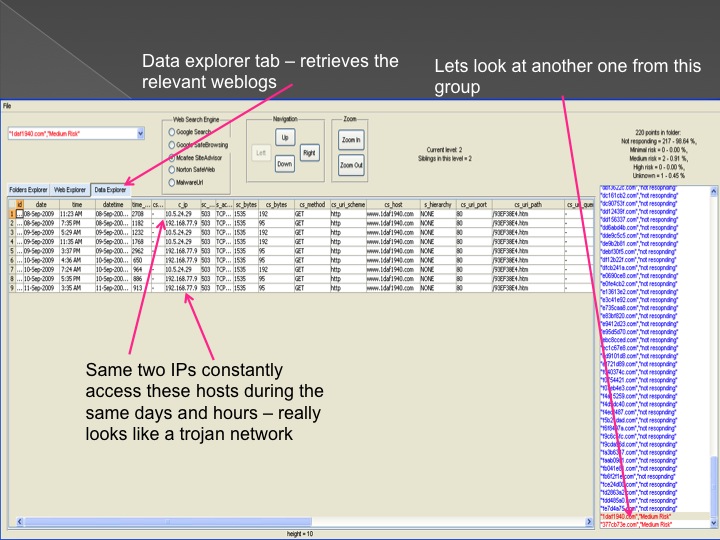
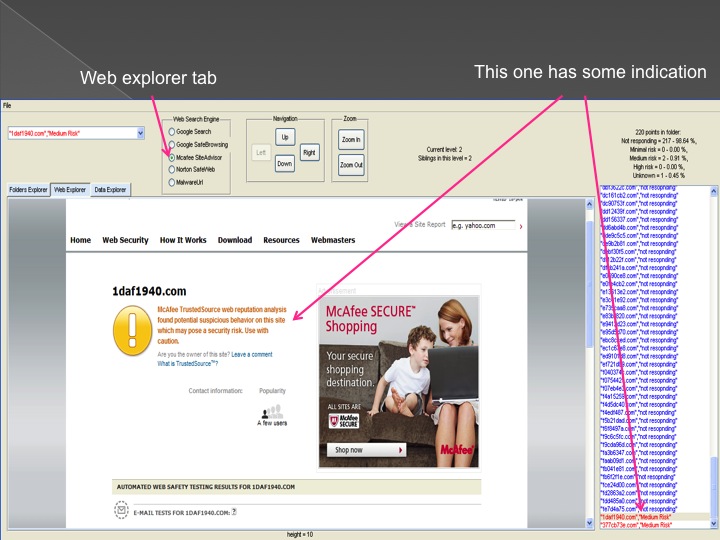
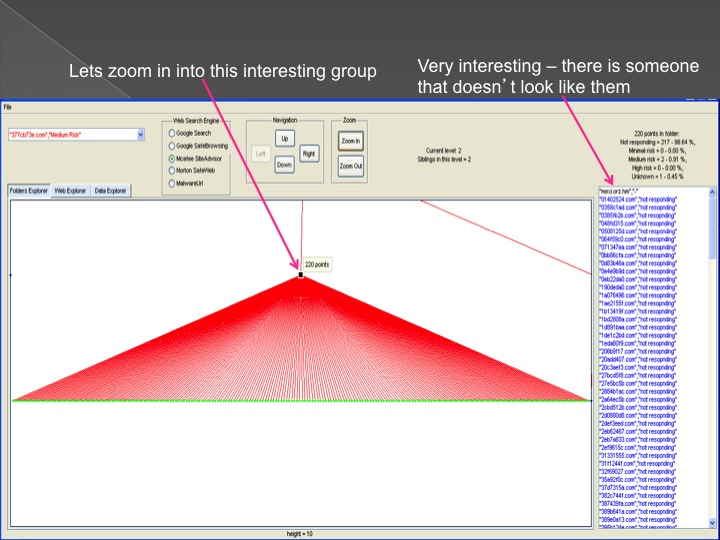
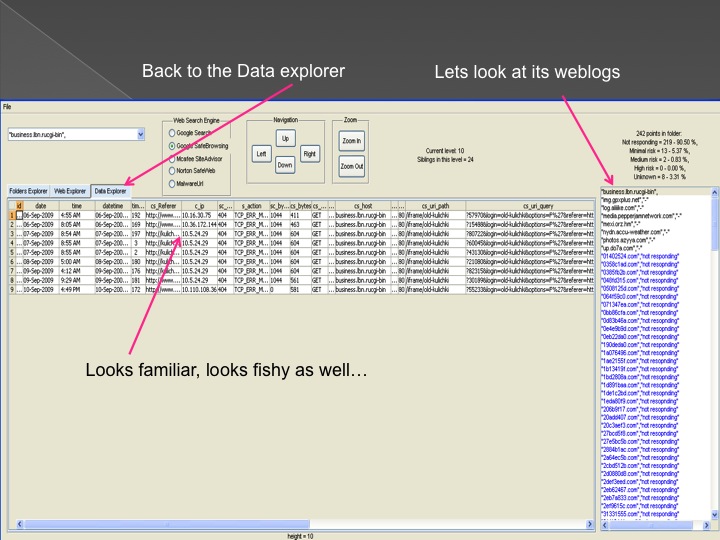
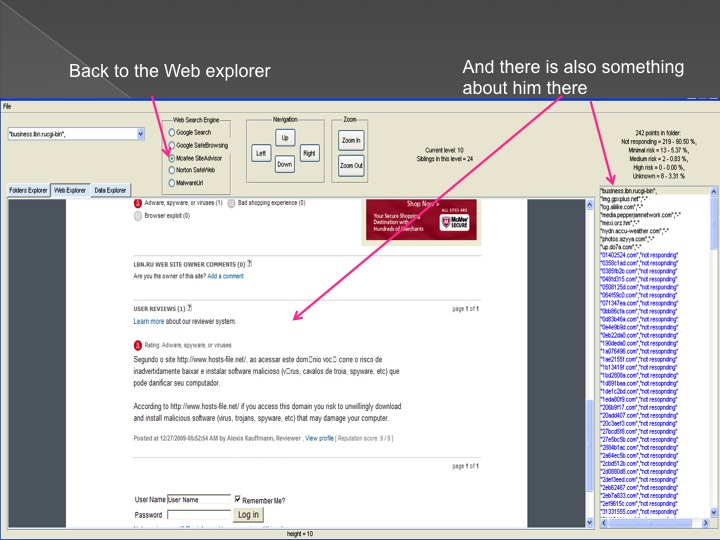
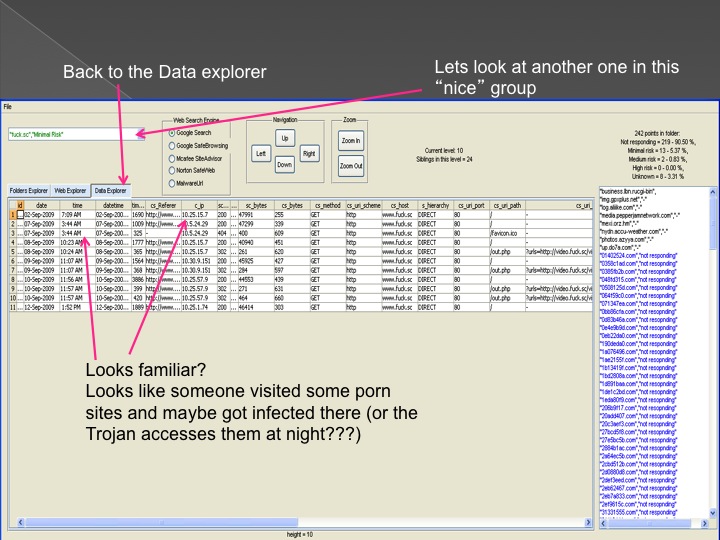
The second method is our Advanced Forensic technology that is used to analyze the detected anomalies, research them automatically, categorize them and
cluster them into groups in an hierarchical structure. Each group represents a family or sub-family of Trojans.
The following series of images presents the process of the advanced forensic:

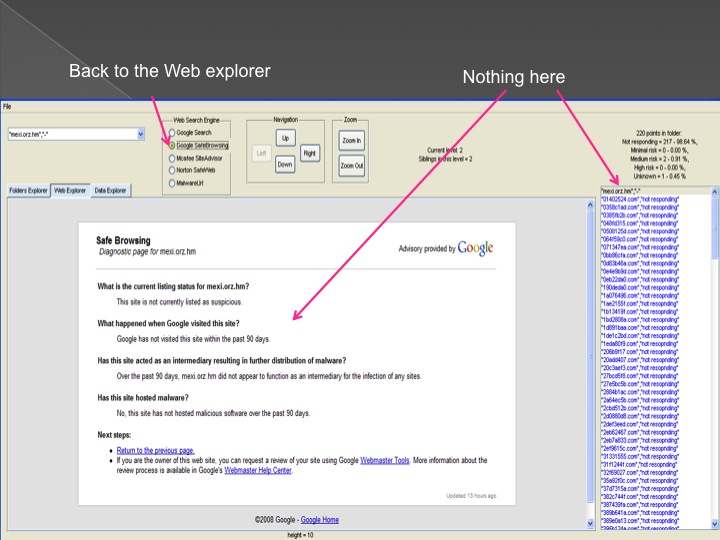
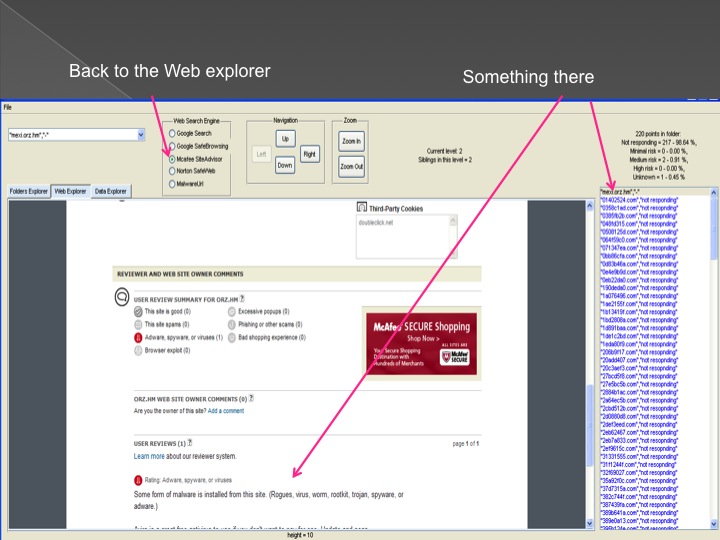
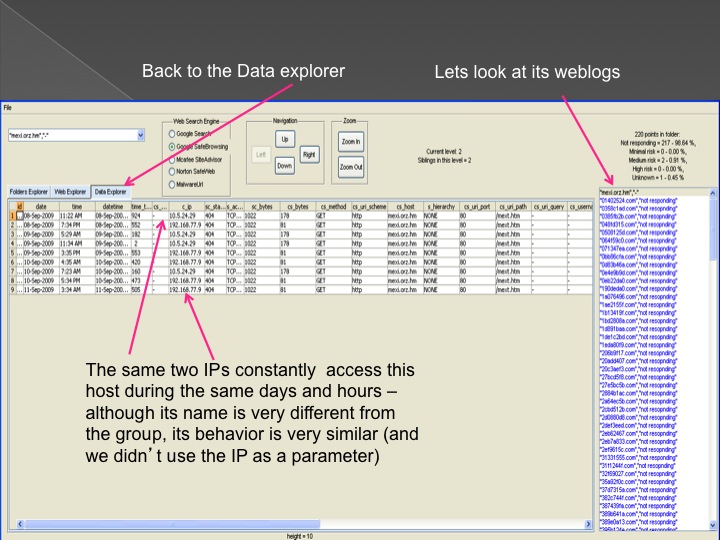
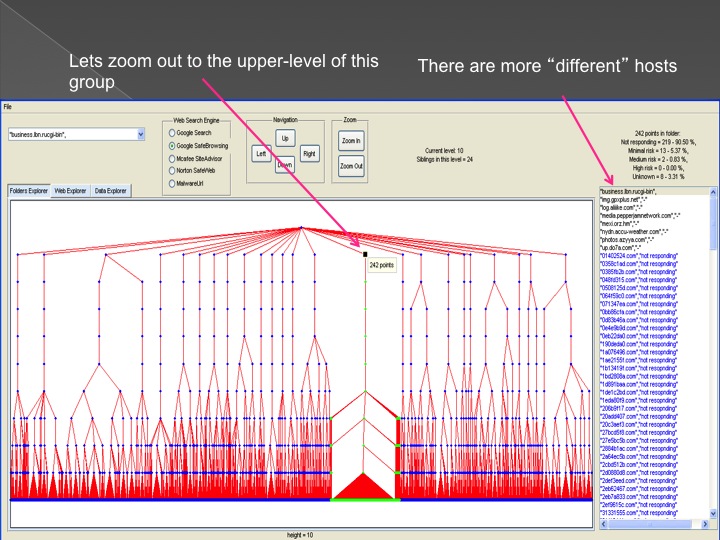
Conclusions and our solution
We developed and used several method for pre-processing of the data and then we used our data mining tools and anomaly detection methods to
identify abnormal activity that can be associated to a stealthy attacker.
The security systems that the ISP uses detected about 50 trojans during the test period. These trojans were related to
different types of trojans (bots, downloaders, backdoors etc,).
We started our analysis with our initial anomaly detection process.
This process detected several major anomalies. We initiated our anomaly characterization process with the most anomalous one in order to detect
other trojans. This process is aimed to automatically learn and characterize the behavior of a specific anomaly, to propagate and diffuse to other unknown anomalies.
This iterative process has the ability to reveal different types and families of anomalies (and in this case, trojans.)
In addition to the already known trojans (the 50 trojans that were detected by the ISP), our system detected more than 3,000 trojans that
were unknown to the security team of the ISP. These trojans were belonged to several families of trojans, including individual Trojans and sophisticated
infrastructures of Trojans. We found out that these highly sophisticated infrastructures of trojans were designed to be undetectable by convential methods and
their target was to steal confident information from organizations.
We developed and adapted a solution for our client. This system enables detection of stealthy attacks and advanced forensic for damage control
and detection of dormant Trojans.